Your First Crypto Vault: A Guide to Trezor Setup & Security
Stepping into the world of cryptocurrencies means taking full control of your digital wealth. This freedom, however, comes with the critical responsibility of securing your assets. Hardware wallets like those from Trezor provide the fortress you need. This guide will walk you through the initial setup at Trezor.io/start and illuminate the powerful features that keep your crypto safe.
Initiating Your Secure Setup
The journey to unparalleled security begins at Trezor.io/start. This official webpage is your central hub for setting up a new Trezor device. Before you even connect your wallet, the site automatically checks for the latest firmware, ensuring you have the most up-to-date protections from day one. It is absolutely vital that you navigate to this site directly and never through a third-party link to avoid phishing scams. The process is designed to be intuitive, guiding you through each critical step with clarity.
Unpacking the Core Benefits and Security
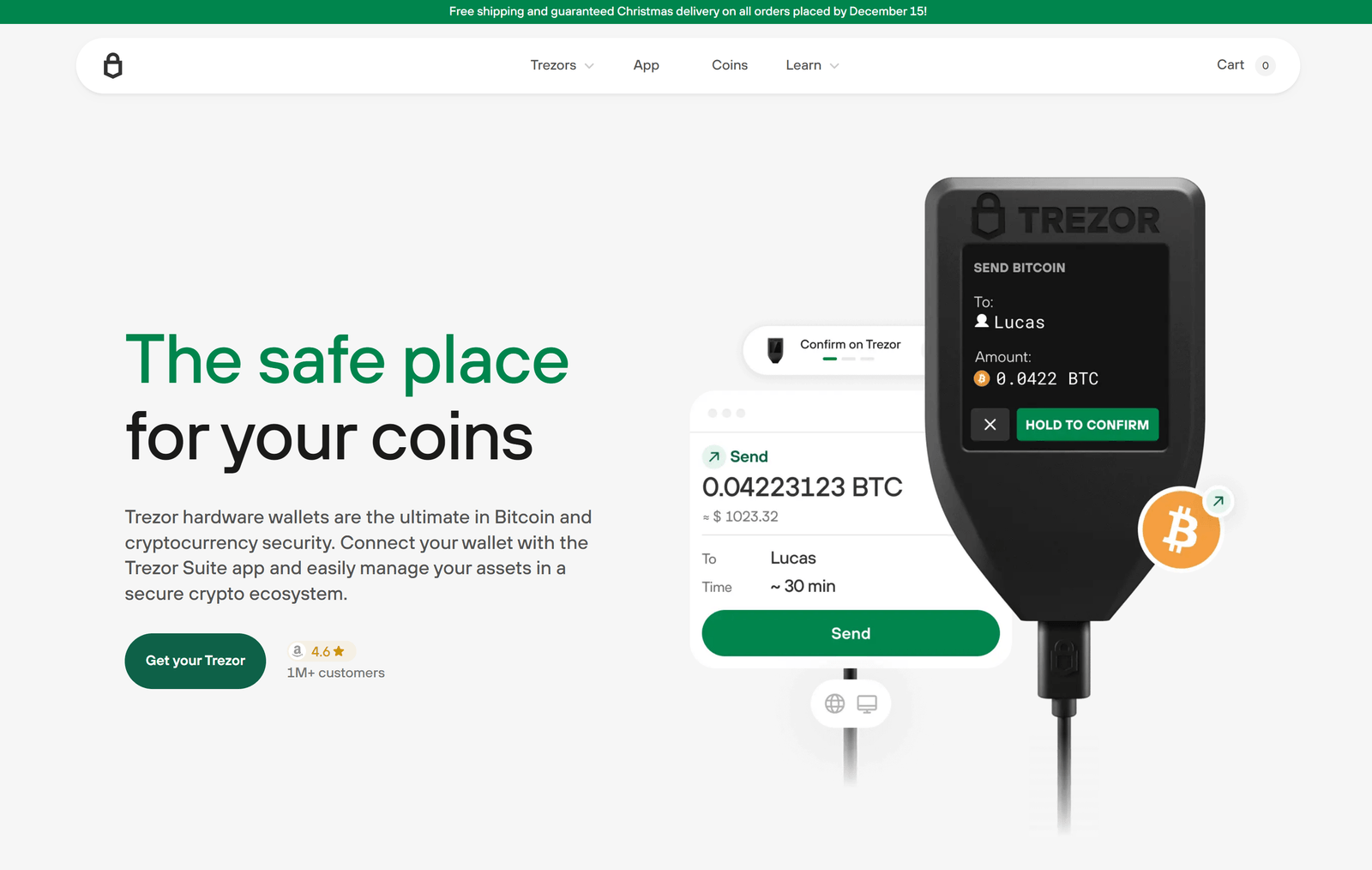
A Trezor device is more than just a storage unit; it’s a self-custody solution. Unlike keeping crypto on an exchange, where you don't control the private keys, your Trezor keeps these keys isolated and offline, safe from online threats.
The cornerstone of its security is the Recovery Seed. During setup, your device will generate a unique list of 12, 18, or 24 words. This seed is your master key. If your Trezor is ever lost or damaged, this phrase alone can restore all your accounts onto a new device. Writing it down on the provided card and storing it in a secure, offline location is the most important step you will take.
Beyond mere storage, the integrated Trezor Suite application allows you to manage over 1,600 coins and tokens, buy and sell assets directly, and monitor portfolio performance—all from a secure desktop interface that doesn’t require exposing your private keys.
Advanced Features for the Modern User
For those ready to leverage the full power of their Trezor, the device offers sophisticated capabilities that go beyond basic holding.
Hidden Wallets with Passphrases: This feature creates a secret, hidden wallet within your standard one. By adding a custom passphrase (a 13th word of your choosing), you can create a "plausibly deniable" wallet. Even if someone were to force you to reveal your seed, they would not be able to access this hidden account without the passphrase.
Staking and Earning Rewards: Trezor Suite supports in-wallet staking for Proof-of-Stake cryptocurrencies like Ethereum (ETH) and Cardano (ADA). This allows you to participate in network security and earn rewards directly from your secure hardware wallet, without transferring assets to a risky third-party service.
SSH and Password Management: Advanced users can employ their Trezor as a secure hardware token for logging into computers via SSH. Furthermore, with the companion Trezor Password Manager, you can safeguard all your online passwords, using your device as the two-factor key to access them.
By starting at Trezor.io/start, you are not just setting up a wallet; you are establishing a personal bastion for your digital future. Its combination of user-friendly setup and powerful, advanced features makes it an indispensable tool for both newcomers and seasoned crypto veterans.